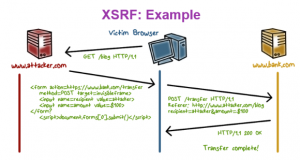
In the web application, the common problem is that all the users inputs are untrusted. Some security measures need to be taken by application to defend themselves from attack. So to handle user access to the application ‘s data and functionality to prevent users from gaining unauthorized access, handling the user input to the application from causing malformed input undesirable behavior, handling attacker and taking suitable defensive measures, managing the application itself by enabling administrators to monitors activities and configure functionality
In any application the central security requirement is controlling the user’ access to its data and functionality. There are different kinds of users some are authenticated users, some are anonymous, some are administrative. The application should be handled so that users can reads the emails own not of others. The following security mechanisms can be used to handle the application.
> Authentication
> Session management
> Access control
Authentication

The authentication mechanisms is basic way to handle the user access. Authenticating is the process of knowing who he/she claims to be. Authentication used in application by basically with the user name and password. In the security critical application like for bank, there can be additional credential or multistage login processes. for the higher security requirement other authentication model may be used based on client certificates, smart cards or challenge response tokens. The authentication process should be carefully handled because any flaws in design and implementation. Flaws can be taken advantages by the attacker to use to guess user name and bypass password and unauthorized access to sensitive data and functionality.
Session Management
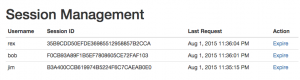
The another task for handling the users are session management. First I want to explain session. After successfully login into application user access different pages and makes series of HTTP request from its browser. At the same time different user some are authenticated and some anonymous try to login the application. So to identify the different users. The application meet the way to create the session for each user and issuing the user a token that identifies the session. Session itself is data Structure held on the server that track the state of the user interaction with application. When the user receive the token, submit it back to the server in subsequent HTTP request enabling the application to associate with that users. When the users does not make request for certain time then the session is expired.
In the term of attack, attacker can use other tokens to authentication and use application. similarly another areas of attack is knowing the how the tokens are generated. Attackers can guess tokens to access different others user tokens.
Access Control
Access control also called authorization is the process to access the particular resources to be granted or denied. Authorization and authentication are different things. From the authentication it can be known the which kinds of the users are and according to the types of users the resources are granted or denied that is authorization or access control. So access control is important part of application. Omitting the access control check part causes attacker to gain unauthorized access to data and functionality.